39+ diffie hellman key exchange calculator
Lets assume that Alice wants to establish a shared secret with Bob. The principle however is the same.

The Raccoon Tls Timing Attack And Minio
Web Steps in Key Exchange.
. Partner 2s public key. Web Diffie-Hellman is an algorithm used to establish a shared secret between two parties. It allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure channel.
You assume the private key for our sender as Xa where Xa q. Let the users be named Alice and Bob. It is used in many different contexts including secure communication protocols virtual private networks VPNs secure file transfer protocols and other.
My guess is not but bear with me. Note that the DHKE method is resistant to sniffing attacks data interception but it is vulnerable to man-in-the-middle attacks attacker secretly relays. They never actually exchange the secret just some values that both combine which let them attain the same resulting value.
Web The Diffie-Hellman key exchange also known as exponential key exchange is a widely used and trusted technique for securely exchanging cryptographic keys over an insecure channel. Web The DiffieHellman DH method is anonymous key agreement scheme. This will be a simplified version of the Diffie-Hellman key exchange in real life better constants and larger variables should be chosen in the form of a game.
Say that a person who could monitor the exchanges could not. The Overflow Blog Coding 102. During this process we will need to generate 5 elements before deriving a shared secret.
This video was created as a part of an assignment. The DH also uses the trapdoor function just like many other ways to do public-key cryptography. Web As a result I know the basics of how the Diffie-Hellman Key Exchange DH from here on works but I dont know why it Stack Exchange Network Stack Exchange network consists of 181 QA communities including Stack Overflow the largest most trusted online community for developers to learn share their knowledge and build their careers.
538 Featured on Meta Ticket smash for status-review tag. Usually the group parameters are what needs to be adjusted over time the most due to computational advances and the advances in cryptanalysis of the discrete logarithm problem DLP. Alice and Bob each compute Same Master Value M.
Partner 2s private key. Web Bob computes Public Value. This group may be mathbb Z_p or may be the points on your favorite elliptic curve usually.
Web Diffie-Hellman operates in a group. Web The Diffie-Hellman algorithm was a stunning breakthrough in cryptography that showed cryptographic keys could be securely exchanged in plain sight. The steps needed for the Diffie-Hellman key exchange are as follows.
Writing code other people can read You dont have to build a browser in JavaScript anymore Ep. Web The DiffieHellman key exchange method allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure channel. Web The Diffie-Hellman Key Exchange is a means for two parties to jointly establish a shared secret over an unsecure channel without having any prior knowledge of each other.
Web Even though Diffie-Hellman key exchange can be used for establishing both public and private keys the Rivest-Shamir-Adleman algorithm or RSA algorithm can also be used since its able to sign public key certificates. Web The Diffie-Hellman protocol is a method for two computer users to generate a shared private key with which they can then exchange information across an insecure channel. Part Deux Related 1 Finding the private key in Diffie Hellman 0 Breaking a modified version of Diffie.
Partner 1s private key. Web diffie-hellman or ask your own question. Conceptually the best way to visualize the.
Heres how it works. First they agree on two prime numbers g and p where p is large typically at least 512 bits and g is a primitive root modulo p. The DiffieHellman key exchange method allows two parties that have no prior knowledge of each other to jointly establish a shared.
It is primarily used as a method of exchanging cryptography keys for use in symmetric encryption algorithms like AES. How does Diffie-Hellman key exchange work. You choose a prime number q and select a primitive root of q as α.
It is one of the earliest practical examples of key exchange implemented within the field of cryptography. Alice and Bob exchange Public Values. Bob computes M A b mod n g a b mod n.
B g b mod n. Web Did you ever wonder how two parties can negotiate a cryptographic key in the presence of an observer without the observer figuring out the key. Web DiffieHellman key exchange DH nb 1 is a specific method of exchanging cryptographic keys.
The algorithm in itself is very simple. Alice computes M B a mod n g b a mod n. Partner 1s public key.
Alice computes M. Web The Diffie-Hellman key exchange is a mathematical protocol allowing 2 people who may have never met to agree on a secret number without disclosing it during their exchanges ie. Web Diffie Hellman Key Exchange Algorithm for Key Generation The algorithm is based on Elliptic Curve Cryptography a method of doing public-key cryptography based on the algebra structure of elliptic curves over finite fields.
To be a primitive root it must satisfy the following criteria. This key can then be used to encrypt subsequent communications using a symmetric-key cipher. Bob computes M.
To implement Diffie-Hellman two end users Alice and Bob mutually agree on positive. The public key can be calculated as Ya. This video explains why key exchange is an issue in cryptography and introduces Diffie-Hellmans solution to this problem.
Web OpenSSL can help you perform a Diffie-Hellman key exchange but it is not directly compatible with this tool. DiffieHellman is used to secure a variety of Internet services.

Diffie Hellman Key Exchange Practical Cryptography For Developers

Diffie Hellman Key Exchange Algorithm Aptitude For Dummies
Network Throughput Calculator How To Calculate Rtt Cisco Community
Diffie Hellman Calculator In Python And My First Story By Vinci Sharma Medium
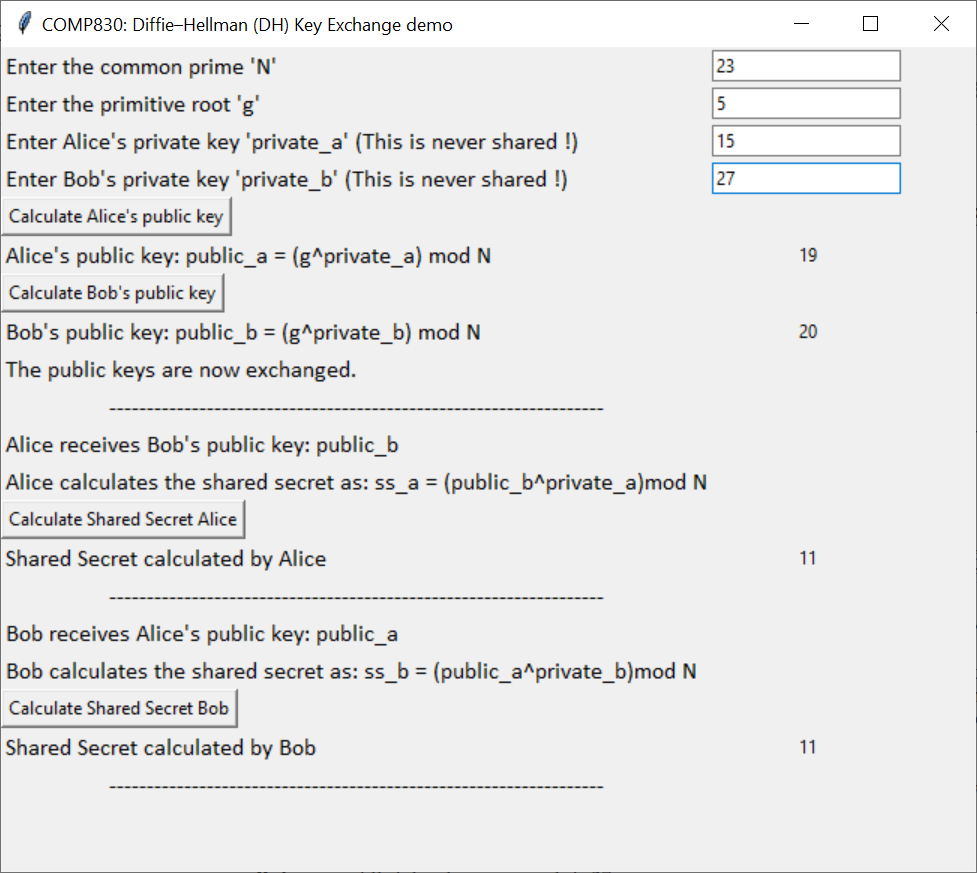
Diffie Hellman Calculator In Python And My First Story By Vinci Sharma Medium

Diffie Hellman Key Exchange Algorithm With Example Youtube

Elliptic Curve Cryptography Ecc Practical Cryptography For Developers
Learning Cryptography Part 2 Diffie Hellman Key Exchange Discrete Log Problem Cyclic Groups By Kerman Kohli Loopring Protocol

Diffie Hellman Key Exchange Practical Cryptography For Developers

Diffie Hellman Key Exchange Protocol Using The Pydhe Python Library The Security Buddy

Diffie Hellman Key Exchange Algorithm Download Scientific Diagram

Learn Dh In Cryptography Diffie Hellman Key Exchange
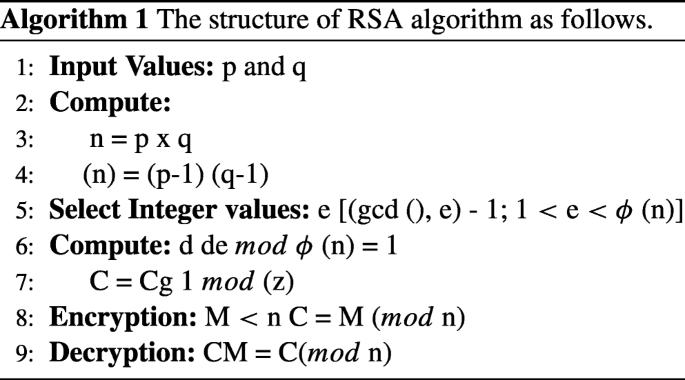
An Optimised Homomorphic Crt Rsa Algorithm For Secure And Efficient Communication Springerlink

Calculator Hackaday

Diffie Hellman Key Exchange Wikipedia

The Diffie Hellman Key Exchange Download Scientific Diagram

Diffie Hellman Key Exchange Css322 L15 Y14 Youtube